Hacking with Kali Linux : A Step-by-Step Instructional Guide to Learning the Fundamentals of Cyber Security, Hacking, and Penetration Testing. Basic Networking Concepts are Included. (2022 Guide) (Paperback) - Walmart.com

Kali Linux Hacking: A Complete Step by Step Guide to Learn the Fundamentals of Cyber Security, Hacking, and Penetration Testing. Includes Valuable Basic Networking Concepts.: Mining, Ethem: 9781672429733: Amazon.com: Books

Kali Linux Hacking: A Complete Step by Step Guide to Learn the Fundamentals of Cyber Security, Hacking, and Penetration Testing. Includes Valuable Basic Networking Concepts.: Mining, Ethem: 9781672429733: Amazon.com: Books










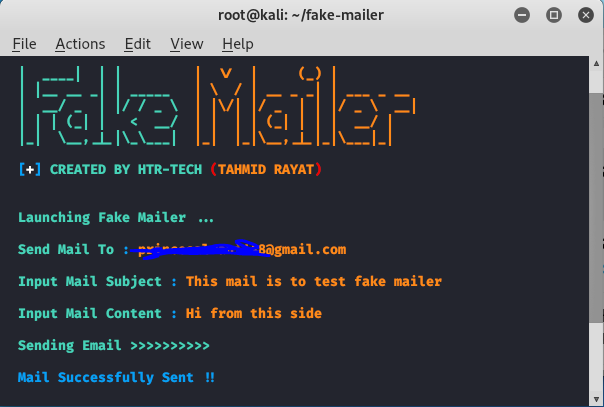
![How to Securely Install Kali Linux on a USB [Guide] | Rapid7 | Rapid7 Blog How to Securely Install Kali Linux on a USB [Guide] | Rapid7 | Rapid7 Blog](https://blog.rapid7.com/content/images/2018/06/Kali-Linux-7.png)

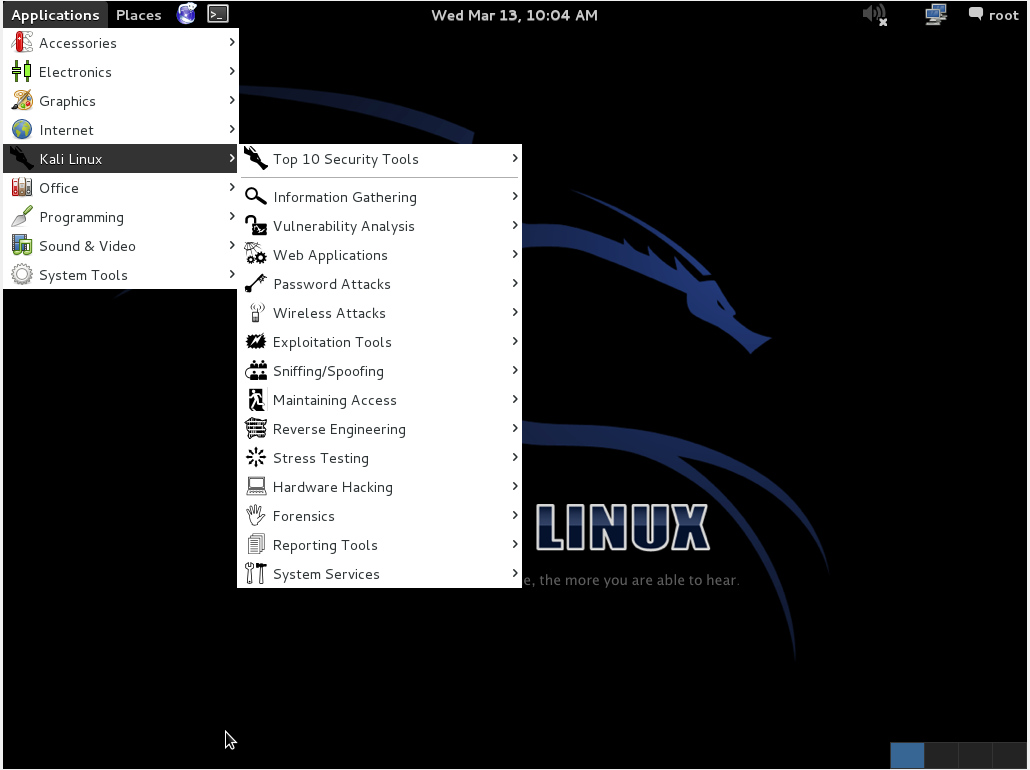



![How to Securely Install Kali Linux on a USB [Guide] | Rapid7 | Rapid7 Blog How to Securely Install Kali Linux on a USB [Guide] | Rapid7 | Rapid7 Blog](https://blog.rapid7.com/content/images/2018/06/Kali-Linux-1.png)